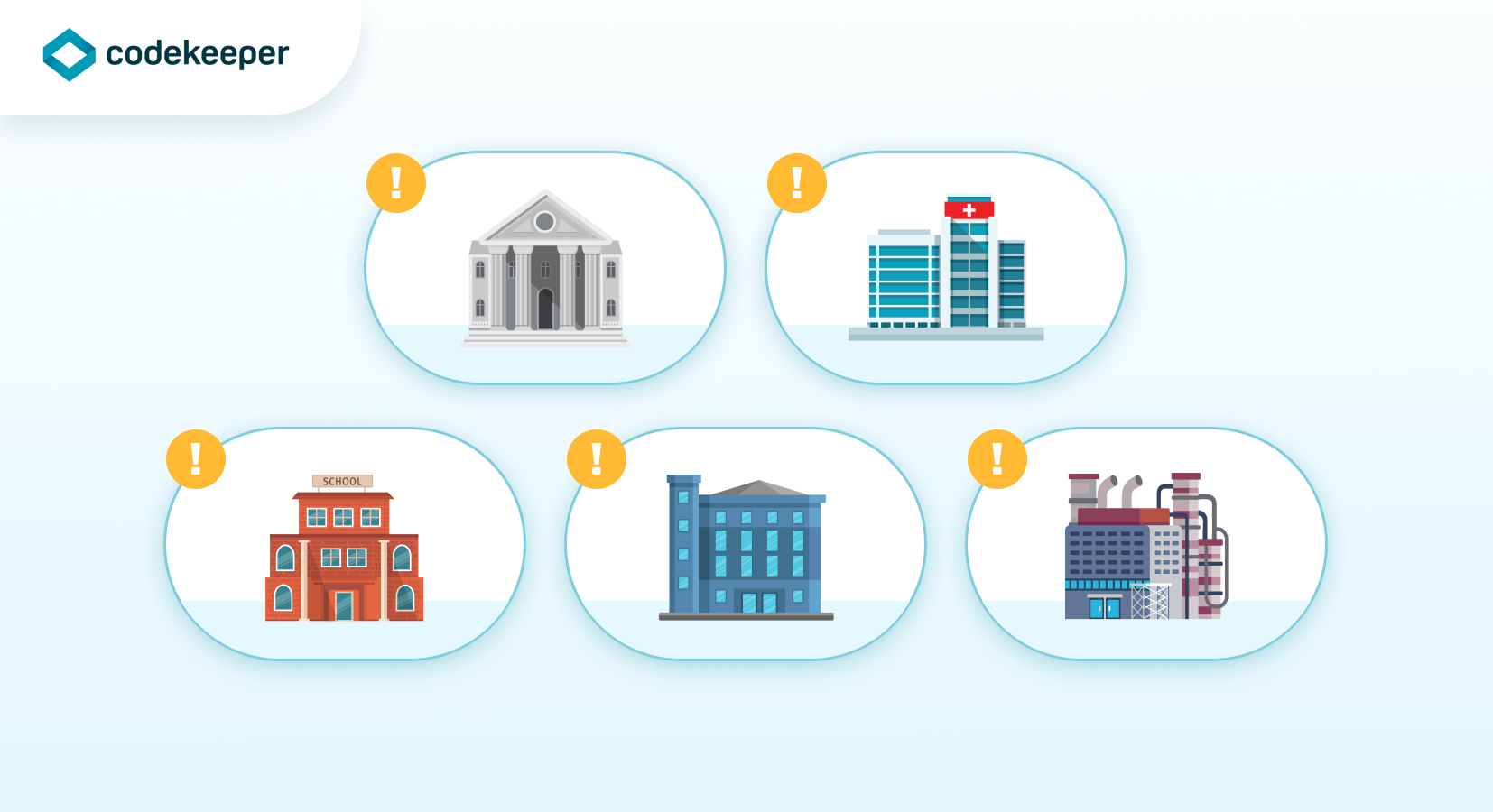
In this modern age, most industries can be vulnerable to ever-lurking hackers looking to make a quick buck. Though there are a few especially targeted industries that threat actors might be interested in due to highly valuable data that translates to potential profitability. In the world of data security, trends show that these 5 industries are at the top of the cybercriminal hitlist.
Jo Rust
Recent Posts
software escrow, saas escrow, software escrow agreements
source code escrow, cyber security
source code escrow, software escrow, saas escrow
When it comes to legal agreements, make sure you know what you're signing for.
Your enterprise relies on mission-critical software and applications that you cannot afford to lose access to as it would result in severe losses in revenue.
You’ve done your research and have decided that it would be in your company’s best interest to enter into a source code escrow agreement. Now the next question you need to ask yourself is: what type of software escrow agreement is best for your business's individual needs?
Although the concept of software escrow agreements is widely recognized, the terminology used in these agreements can still leave one scratching your head.
Let’s have a look at the different types of agreements:
enterprise, source code escrow
Consider the following.
We’re heading into a new year and your business is thriving. Congratulations! There is no doubt that you have worked hard to get to where you are today. You’ve invested time and money in your people and resources and you’ve finally found the winning recipe. Your impressive annual sales reports are evidence of a business well run. You use state-of-the-art software solutions that give you the upper hand over your competitors.