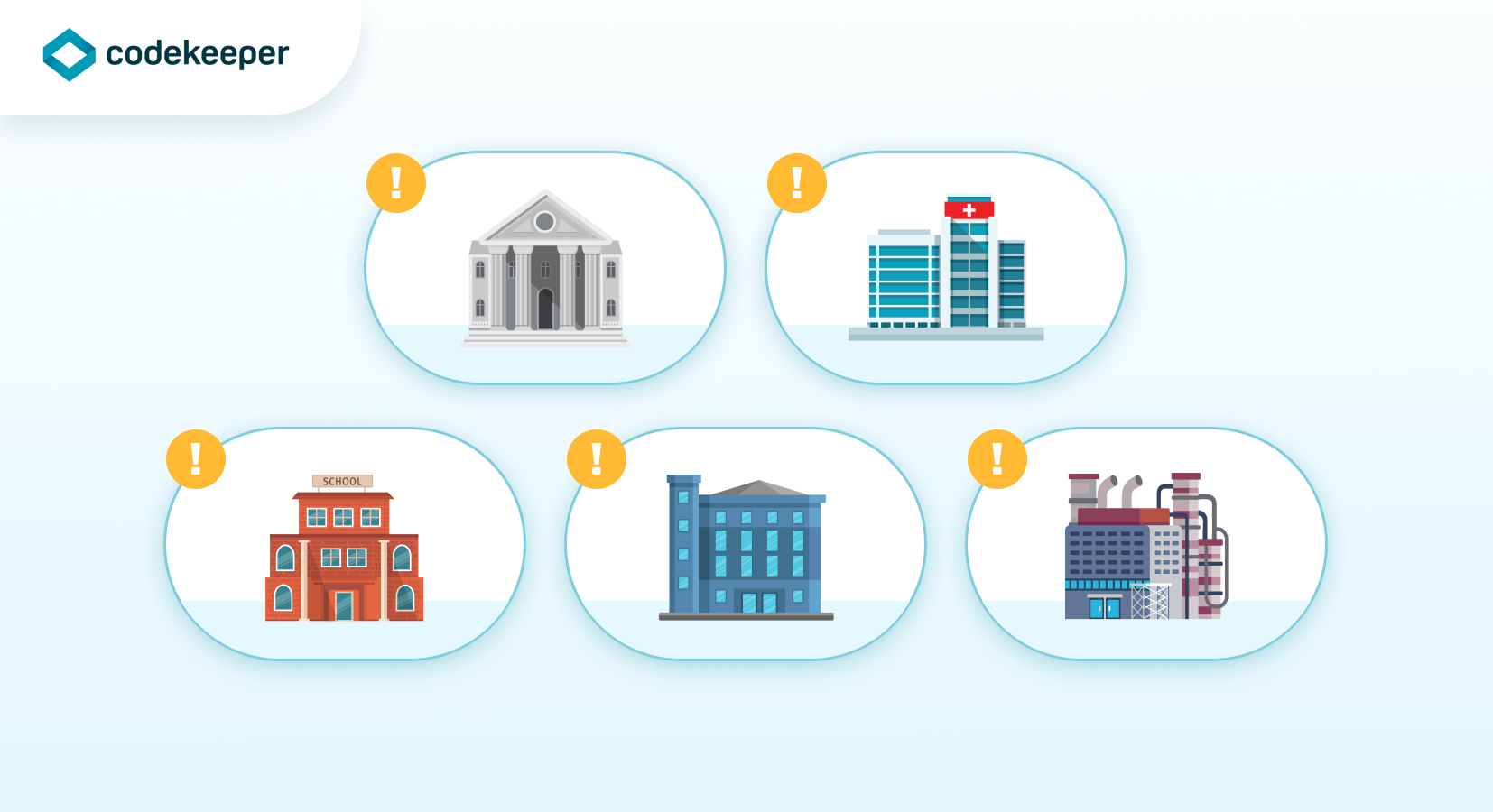
The Top 5 Most Vulnerable Industries In Need Of Software Escrow
These are the top 5 most vulnerable industries in need of software escrow due to the increase in cyber threats.
By Jo Rust
In this modern age, most industries can be vulnerable to ever-lurking hackers looking to make a quick buck. Though there are a few especially targeted industries that threat actors might be interested in due to highly valuable data that translates to potential profitability. In the world of data security, trends show that these 5 industries are at the top of the cybercriminal hitlist.
Software escrow can help to stop threat actors in their tracks
1. Financial Services
It is no surprise that financial services should be in the number one spot. With technological advancements in the industry, more and more banks and other financial services providers are struggling to keep up.
Implementing stringent security best practices is required by numerous industry standards, which means that threat actors need to become really creative when targeting this industry.
The area most at risk is web application security. It is extremely hard to detect infiltrations from cyber criminals as millions of clients access these applications simultaneously. It is estimated that about 44% of all infiltrations are due to insider activity.
The average cost of a data breach in the financial sphere: >$10 Million
2. Healthcare and Pharmaceuticals
The healthcare industry has paid the highest data breach cost of any industry in the last 11 years. Suffice it to say that it is a favorite among organized cybercrime syndicates. In our previous blog post, we looked at some of the most recent attacks on hospitals in both France and the United States. You can read about it here.
The main reason that this industry is a hot favorite can be attributed to the value of data stored by the industry. Patient information, medications, medical programs, etc. Threat actors can sell stolen patient information, or gain unauthorized access to prescription medications. In recent years these criminals have been wreaking havoc on this industry.
The very distinct difference here is that such threats can lead to hospital systems and equipment shutdowns, leading to a rise in patient mortality rates. The healthcare and pharmaceutical industry can really benefit from data escrow services and data processing agreements for HIPAA.
The average cost of a HIPAA violation penalty: $100 - $25 000 per violation
`
Secure your mission-critical data with Codekeeper
3. Education
The COVID-19 pandemic has led to a surge in the popularity of hybrid and online education. While some educational institutions have yet to adapt to new realities such as cloud storage, online documentation, and digital data sources, many higher-education institutions now cope with data leaks or breaches more often than they did before.
In 2022, social engineering took first place among the data breach patterns in education. Pretexting was the leading method of social engineering by attackers who used this technique to instigate fraudulent funds transfers by luring victims into tricky conversations. Instead of ordinary phishing techniques, this new hacking method uses creative emails to make victims respond as desired.
The average data breach cost in the educational sphere: >$3.79 Million
4. Government Agencies
Governments are vulnerable to cyberattacks, which can be used for financial gain or espionage. Malicious actors could breach a government database to obtain strategic information, such as military and communication infrastructure data.
Governments hold large amounts of PII, which motivates hackers. The 2020 SonicWall Cyber Threat Report revealed that cybercriminals shifted their focus to local, state, and federal governments in 2021. Ransomware, cryptojacking, and IoT malware were among the leading types of governmental attacks.
The average cost of a data breach in the public sector: $1.93 Million
5. The Energy Industry
Hackers may seek more than money and data. A widespread power outage, one that affects millions of citizens, can show the world just how much control hackers can have over our lives. If they can successfully access entire power grids or nuclear facilities, the results could be detrimental.
According to a recent report by FireEye, threat actors and “hacktivists” will target energy companies in response to perceived controversies. As these critical infrastructures become more connected and increasingly reliant on technologies, they may become more vulnerable.
In 2021, the largest fuel line in the US was taken offline, which resulted in fuel shortages along the entire East Coast.

How Can You Protect Yourself?
Train your employees
Employees cannot possibly keep themselves up to date with security best practices relating to ever-evolving cyber threats. Provide training to help your staff remain alert and minimize the risk of phishing and other hacking strategies.
Research software escrow companies
Placing mission-critical data and source code into escrow with a software escrow agent is another way of maintaining business continuity. Have a look at the escrow solutions we offer.
Assess 3rd Parties
It is important to make sure that your third-party vendors have strong cybersecurity as well. This can be done by exploring 3rd Party Dependencies Escrow Agreements. Investing in an escrow agreement will cost a business far less than the average hefty $4.3 million price tag that comes with a data breach.