Enterprise Risk Management (ERM): What It Is and Why You Should Care Part 3
Every decision we make involves some sort of risk. How do we define an enterprise-level risk?
By Content Team
Table of contents:
Minimizing enterprise risk with software escrow.
The last recommendation above is an often-overlooked solution that has become critical in today’s age of digitalization.
The advent of the digital age brings a wide range of opportunities, but also many potential pitfalls—namely with source code and data responsible for running these systems. This puts enterprises at tremendous risk that could sink them in the long run.
Ask yourself: What would happen to your business if you were to suddenly lose access to your software?
We live in unprecedented times, and now it’s more important than ever to ensure that your mission-critical systems are secure and always available. This is why a growing number of companies worldwide are turning to source code escrow to protect themselves from unpredictable events, such as their code suppliers going out of business or discontinuing maintenance and support of software.
This brings inherent risks to organizations both large and small — not only in terms of potential cyber-attacks but also loss of data and source code access. And in response, investors and regulatory bodies are increasingly mandating companies throughout many industries to scrutinize and report on the effectiveness and efficiency of their risk-management policies and procedures.

Why source code escrow is essential to organizations
Any company that licenses software, outsources software development, or hosts its software on a cloud or external data center should consider securing their source code and related data using escrow.
Here are just some of the potential problems that could have catastrophic consequences on your business with no escrow in place:
- Counterparty risk
- Losing data accidentally
- Supplier going bankrupt
- Stolen data
- Unwanted downtime
- Unpredictable external events (e.g., COVID-19)
- Backup recovery snafus
- Data and identity theft
- Hacking ransomware
- Employee sabotage
- Senseless and wasteful lawsuits
Unfortunately, this list only scratches the surface. After losing control of data and source code, all the sound business practices in the world won’t save an organization from ultimate doom.
Considering the number of software providers defaulting due to the COVID-19 crisis in 2020, companies around the world are making it a priority to secure their access to source code with an adequate escrow.
With modern escrow solutions such as Codekeeper on the market, you don’t have to choose between quality and price; Codekeeper is a market leader both in terms of technology and price.
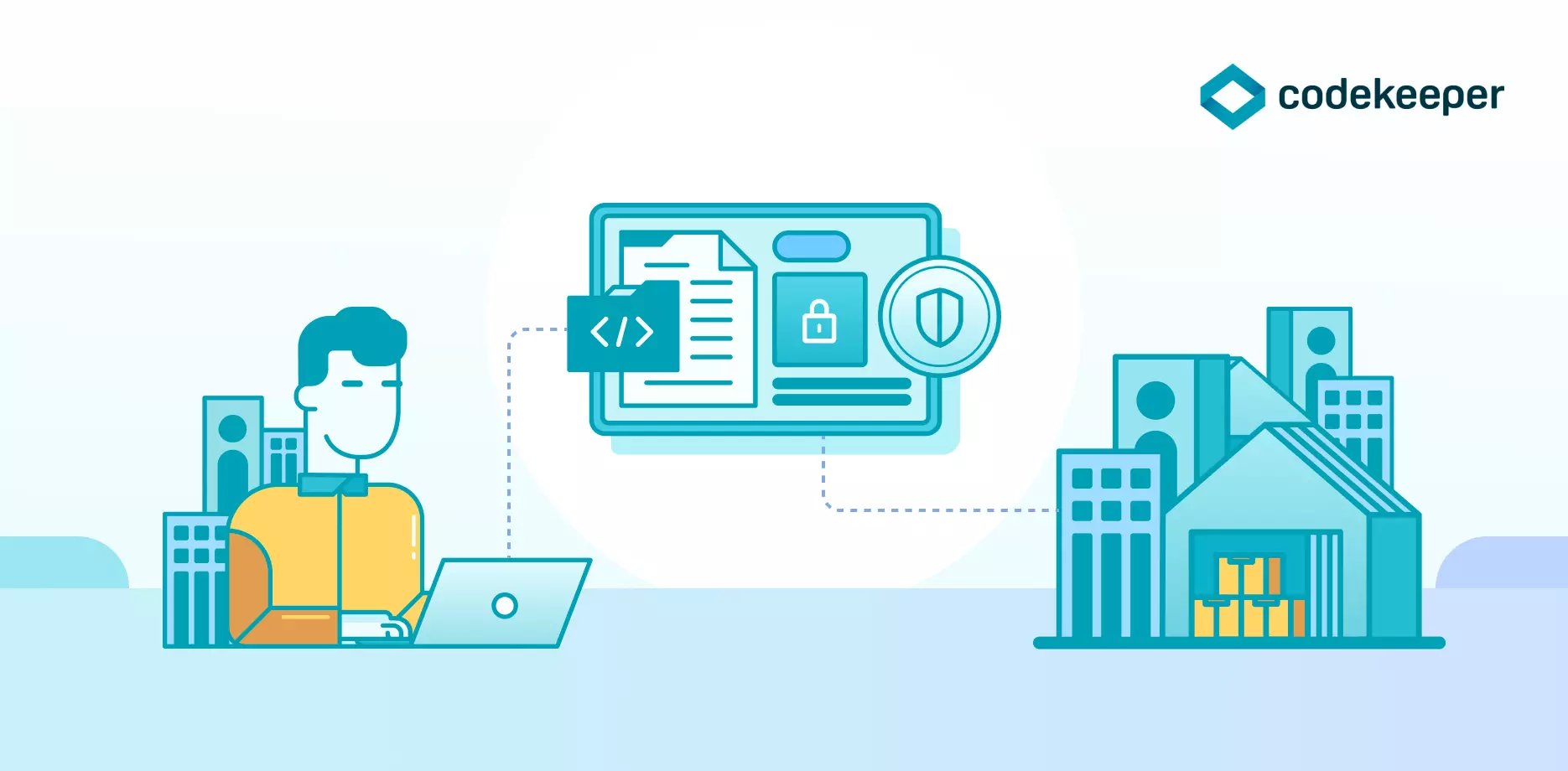
How does source code escrow work?
In a nutshell, software escrow is a service that helps protect all parties involved in a software license by having an independent, neutral 3rd party escrow hold source code, data, and documentation until a mutually-agreed-upon event occurs.
This independent and neutral storage is the key to mitigating risk to all parties involved. The process is simple:
I. Execute an escrow agreement with a trusted escrow provider
When deciding which software escrow vendor to use, some important considerations include technology they use, automation capabilities, integrations with developer platforms, legal expertise, and ease of use.
II. Deposit source code and other desired materials to escrow
Source code, data, documentation, and any other important materials are deposited into escrow. You should look for a modern escrow provider that allows for escrow synchronization, automated submission scripts, and deep integrations with developer platforms to ensure efficiency and adequate security.
III. Automatically update escrow as the software product evolves
As software continues to evolve and new versions are developed, source code escrow must be updated simultaneously. Unlike traditional escrow providers, modern solutions automate this process to ensure your materials are always up-to-date.
IV. Release escrow materials in case release events occur
Release terms define the conditions under which the software escrow provider should release escrow materials to the licensee. This ensures that the materials are only released to the licensee after an event that all parties have agreed upon in advance.
Tip: If you want to learn more about what a software or source code escrow is, how it’s used, and how it might benefit your company, check out this guide for everything you need to know to get started.
Setting up source code escrow can seem daunting, especially when it's new to an organization. Our mission here at Codekeeper is to make this process as seamless as possible for your organization.
Our platform seamlessly integrates with developer workflows on SCM-platforms like Github, saving you time and cutting your costs. And unlike traditional escrow providers, Codekeeper ensures your source code and data deposits are encrypted and fully automated, so they’re always up-to-date and in compliance.
Codekeeper also includes official escrow agreements, release terms, beneficiary management, data escrow, and an arsenal of other services. And last but not least, thanks to our unique automation technology, we also offer the best price guarantee. You can learn more about our pricing model here.
Join leading global brands and tech companies, who are ditching traditional escrow providers and turning to modern solutions such as Codekeeper. With our superior technology and pricing, you can ensure that your mission-critical systems remain unaffected through any circumstance.
Scale up your source code and data security with Codekeeper! Automatically deposit materials, streamline your escrowing processes, and cut costs with Codekeeper.



